Introduction
LDAP authentication for the JOC Cockpit is offered from the JS7 - LDAP Identity Service and relies on a connection between the JS7 - REST Web Service API and the LDAP Server.
- Early JS7 releases make use of JS7 - Shiro Identity Service, for migration see JS7 - Shiro Identity Service Migration.
- The connection to the LDAP Server be secured, see JS7 - LDAP over TLS (STARTTLS) and LDAP over SSL (LDAPS).
This article describes the steps for configuration with an LDAP Directory Service:
- Step 1: LDAP Configuration
- Step 2: Authentication
- Step 3: Authorization
- Define roles
- Define groupRolesMapping
- Define the LDAP attribute search for groups
Relevant Tools
- An LDAP Browser:
- The screenshots used in this article were made with the Softerra LDAP Browser that was configured to use the relevant LDAP Directory Service.
- A command line utility:
- The examples used in this article are executed with ldapSearch.
Proceeding
The following diagram provides an overview of the setup proceeding:
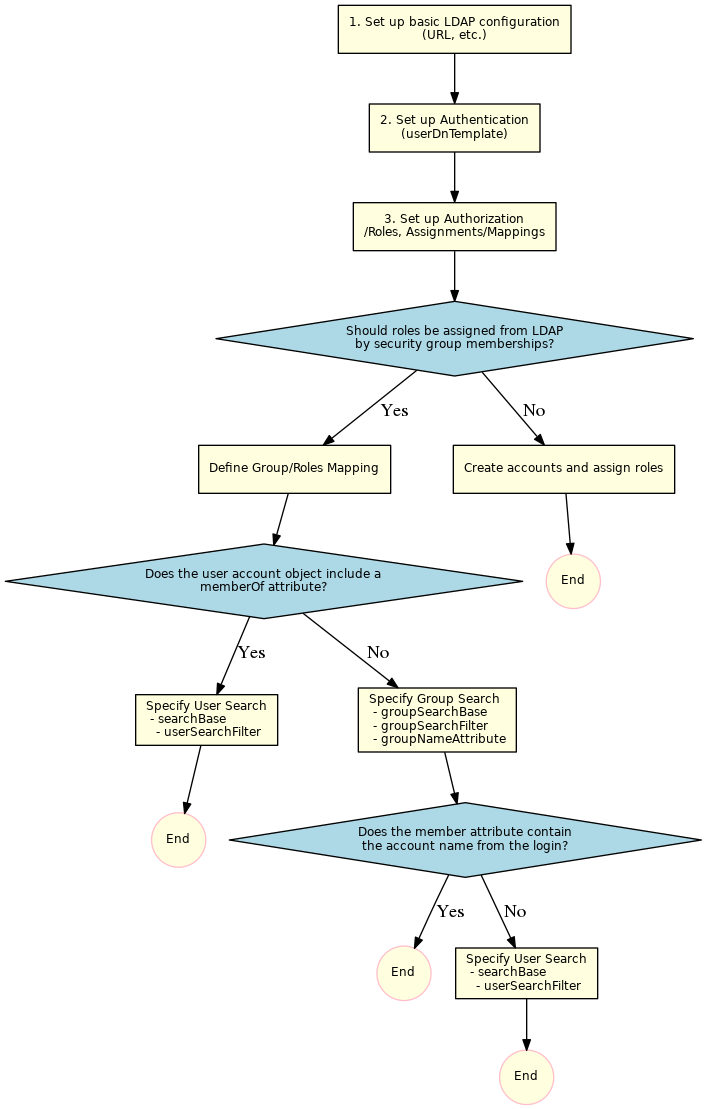
Step 1: Basic LDAP Configuration
The LDAP configuration can be managed from the Administration->Manage Identity Services view like this:
Add Identity Service
In a first step click the Add Identity Service button that brings up the following popup window.
- A Name has to be specified that identifies the LDAP Identity Service.
- The Identity Service Type gives a choice
LDAP: to map user/role assignments from security group membership in the LDAP Server,LDAP-JOC: to manage user/role assignments from the Identity Service.
- Do not make the Identify Service Required before you are certain that the service configuration works fine.
- Select the
single-factorAuthentication Scheme.
Manage Identity Service Settings
In a next step set up the configuration of the service:
- Select the Manage Settings action menu item like this:
This brings forward a popup window with the following tabs:
- Simple Mode: The most frequently used settings are available.
- Expert Mode:: The full set of settings is available.
Specify General Settings
The following table lists the general items used to configure an LDAP connection.
| Name | Value | Description |
|---|---|---|
LDAP Server URL |
| The host and the port of the LDAP Server. |
LDAP Start TLS | true|false | To enable Starttls set the value to Please note that the server must be prepared to serve with StartTls. To check this, you can use an LDAP browser. Configure your LDAP Server there and click the "Enable Starttls Button" On client side you will need the certificate and you have to add the certificate to your truststore. The path to your truststore is defined in the
Example values:
Note: we habe had difficulties when using Starttls with the JRE 1.8.0_151 and have overcome these by installing the corresponding JDK. |
Host Name Verification | true|false | Enables the host name verification of the certificate. The default value is off. |
LDAP Truststore Path | ||
LDAP Truststore Password | ||
LDAP Truststore Type |
Step 2: LDAP Authentication
Specify Authentication Settings
The following table lists possible values for authentication with an LDAP Server:
The value {0} will be substituted with the account name.
| Name | Value | Description |
|---|---|---|
LDAP User DN Template |
| Should work from scratch for Microsoft Active Directory®. For login use |
uid={0},ou=People,dc=sos | Use with Microsoft Active Directory® and other LDAP Servers. Look up the For login use | |
cn={0},ou=Users,dc=sos,dc=berlin,dc=com | Use with Microsoft Active Directory® and other LDAP Servers. The Common Name For login use | |
uid={0},dc=example,dc=com | Use with Public LDAP Server. For login use |
Verify Authentication Settings
Verify by use of LDAP Browser
Possible values for the LDAP User DN Template can be derived from an account's properties. The below screenshot displays such properties from an LDAP Browser:
In a first step search with the value from the LDAP User DN Template in the Search DN input field. The query should return only one entry.
From the properties of the resulting entry the setting for the account is used and the uid value is replaced with: {0}.
Verify by use of ldapSearch
Users can check the value of the LDAP User DN Template setting by use of the ldapSearch utility:
Example for use of a public LDAP Directory Service
The following example uses a publicly available LDAP Server. To our experience this server provides a good example to make an initial LDAP configuration work.
Note:
The option -x is used in the ldapSearch examples in this article. It is possible that an LDAP Directory Service does not allow this option and instead an account and a password have to be specified. In this case the command would look like this:
ldapsearch -h ldap.forumsys.com -p 389 -b "uid=gauss,dc=example,dc=com" -W -D "uid=gauss,dc=example,dc=com"
Verify by use of JOC Cockpit
Try to login with an LDAP Account/Password combination. Use an Account that you have verified to be correct by executing the ldapSearch command described above. If there are no Role(s) configured for the Account but the authentication works then you will see the following screen that complains about missing authorization after successful authentication:
Step 3: Authorization
Authorization includes the assignment of roles to user accounts. Roles, in turn, hold permissions. For details see JS7 - Manage Roles and Permissions.
There are two options for assignment of roles to user accounts depending on the Identity Service Type:
LDAP: add a Group/Roles mapping: membership of a user account in a security group of the LDAP Server is mapped to a role in the Identity Service.LDAP-JOC: add a user account and assign roles. Accounts are managed with the Identity Service in parallel to the LDAP Server. No user passwords are managed with JOC Cockpit as authentication is performed with the LDAP Directory Service.
Assign Roles with Identity Service
For details see JS7 - Manage Roles and Permissions.
Map Roles from LDAP Security Groups
If the Roles are assigned with the JOC Cockpit Identity Service Management by using the Identity Serviced LDAP-JOC, then you can skip this chapter.
The group roles mapping defines a search for groups and a map that assigns these groups to a role.
The search for groups can be executed with one of these options
- The Account has a memberOf attribute. Then you can retrieve the list of groups with the User Search. Then proceed with Using memberOf with User Search.
- The Account does not have a memberOf attribute. The group contains the Accounts that are members of the group, Then proceed with Using Group Search.
These options cannot be mixed!
With the founded groups a map is defined, that maps the groups to roles.
In both searches the account can be substituted
How substitutions will be done
In the groupSearchFilter and the userSearchFilter you can specify %s e.g.
(uid=%s)
The %s will be substituted with the account from the login. If you login with domain\account oder account@domain the value for the user is account.
You can specify ^s e.g.
(uid=^s)
The placeholder ^s will be substituted with the original value from the login e.g. account@domain.
Usersearch
This approach looks for the Account entry and reads the memberOf attribute. This attribute is often used when, for example, configuring Microsoft Active Directory® LDAP servers.
Define a userSearchFilter and a searchBase that will find the account .
Microsoft Active Directory® that supports memberOff attribute
| Name | Value | Description |
|---|---|---|
LDAP Search Base |
| The search base for the ldap search |
| LDAP User Search Filter | Default: (sAMAccountName=%s) |
General
| Name | Value | Description |
|---|---|---|
LDAP Search Base |
| The search base for the ldap search |
| LDAP User Search Filter | Example: (uid=%s) |
Groupsearch
Microsoft Active Directory® that supports memberOff attribute
General
Group Roles Mapping
The mapping is defined in the expert tab of the LDAP Identity Service Manage Settings view.
Note that the value of the group depends on the result of the group search. It is the value of the attribute that you have specified with the groupNameAttribute. Default for the groupNameAttribute is memberOf. This indicates that if you are retrieving group memberships by use of the memberOf attribute of an account then you have to specify the complete value of the memberOf attribute value, i.e. the distinguished names of group hits.
Example for Group Mapping with Microsoft Active Directory by memberOf Attribute
A typical mapping when using Microsoft Active Directory with the memberOf attribute for group memberships includes to specify group hts by their distinguished name like this:
CN=Group1,OU=SpecialGroups,OU=Groups,OU=Company,DC=sos-berlin,DC=com ==> allCN=AnotherGroup,OU=SpecialGroups,OU=Groups,OU=CompanyDC=sos-berlin,DC=com ==> adminitratorCN=Beginners,OU=SecurityGroups,OU=Groups,OU=Company,DC=sos-berlin,DC=com ==> business_user
Example for Group Mapping by cn Attribute
A mapping that is based on group search would identify group hits by the value of their common name like this:
sos ==> it_operatorapl ==> administrator,application_manage
a) Using memberOf with User Search
If the Account entries do not have the memberOf attribute then you can skip this section and proceed with Using Group Search.
Settings:
ldapRealm.searchBaseldapRealm.userSearchFilter
This approach looks for the Account entry and reads the memberOf attribute. This attribute is often used when, for example, configuring Microsoft Active Directory® LDAP servers.
Define a userSearchFilter and a searchBase that will find the account (%s will be replaced by the Account name from the login without the domain part).
Example for User Search
ldapRealm.searchBase = ou=People,dc=sosldapRealm.userSearchFilter = (uid=%s)
Example for User Search in Active Directory®
ldapRealm.searchBase = dc=example,dc=comldapRealm.userSearchFilter = (sAMAccountName=%s)
An LDAP Browser can be used to get the correct values for the searchBase and the userSearchFilter. Perform a directory search with the values. You should find only one entry.
The searchBase is the value of the base DN (or ParentDN in the screenshot above).
Hint: if the attribute name in your environment is not the default memberOf then you can specify the name of the attribute with the groupNameAttribute key as described in the next section.
b) Using Group Search
If the Account entries have the memberOf attribute then you can skip this section and proceed with Using memberOf with User Search. Settings:
ldapRealm.groupSearchBaseldapRealm.groupNameAttributeldapRealm.groupSearchFilter
After defining the Group Search the shiro.ini configuration file will look like this:
When the memberOf attribute is not available for the Account then you can use the Group Search.
Define the groupSearchBase and the groupSearchFilter. For example:
ldapRealm.groupSearchBase = ou=Groups,dc=sosldapRealm.groupSearchFilter = (uniqueMember=uid=%s,ou=People,dc=sos)
Getting the value for the groupSearchBase
Identify the location where the groups are stored. This is your groupSearchBase.
Getting the value for the groupSearchFilter
Click one group Entry (in the screenshot, cn=apl) and see how the members are stored there.
The groupSearchFilter is configured with attr=val where attr is name of the attribute and val is the content. In this example, the attr is uniqueMember and the val uid=%s,ou=People,dc=sos, where the userid is replaced with %s. This results in:
ldapRealm.groupSearchFilter = (uniqueMember=uid=%s,ou=People,dc=sos)
Verifing the groupSearchFilter with the ldapSearch command
ldapsearch -h localhost -p 389 -b "ou=Groups,dc=sos" -s sub "uniqueMember=uid=ur,ou=People,dc=sos" -x
This search should return the group entries the Account is a member of. Identify the attribute containing the group name that is to be used in the user roles mapping. This can be seen in the next listing
Verifing the groupSearchBase and groupSearchFilter with an LDAP Browser
groupSearchBase and groupSearchFilter values by using them to perform a directory search. The result should show all groups the account is a member of.Now set the groupNameAttribute to the name of the attribute that contains the group name.
ldapRealm.groupNameAttribute = cn
Hint: The complete content of this attribute must be used in the groupRolesMap attribute. Typical content of the attribute could be ou=Groups,dc=sos,cn=groupname .
Substitution of the account name
If the roles are assigned with the JOC Account Manager (i.e. there is a [users] section in the shiro.ini configuration file) you can skip this chapter.
If the value of the member of the groups contains the Account name from the login then you can skip this chapter
Sometimes the values of the member do not contain the Account Name from the login but, for example, the cn of the Account. In this case you have to search for the Account first and then specify the name of the attribute that should be used instead of the Account name from the login .
To achieve this, specify a searchBase, a userSearchFilter and a userNameAttribute.
ldapRealm.searchBase = ou=People,dc=sosldapRealm.userSearchFilter = (uid=%s)
Verify by use of ldapSearch
This search should return the Account with the given Account name. Identify the attribute that should be used for substitution in the Group Search base if it is not the Account name from the login.
Verification by use of LDAP Browser
Perform a directory search with your LDAP client to check the User Search configuration. You should find only one Account entry with the given Account name.
Then identify the name of the attribute that contains the value for substitution. For example:
ldapRealm.userNameAttribute = cn
The configuration will look like this:
Examples and special configurations
Example LDAP Configuration with mixed LDAP and Shiro Authentication
Add the iniRealm to
securityManager.realms = $ldapRealm, $iniRealm
Behavior Notes:
- By default roles from the shiro ini are added to the roles of an authenticated LDAP user with the same name. This happens regardless of whether or not a password is set for the account in the shiro ini file. However, a number of options can be configured to modify this behavior. These are described in the Multi-Realm Authentication and Authorization article.
Example LDAP Configuration for Active Directory with mixed LDAP and Shiro Authentication
Login with sAMAccountName specified for domain\account or account@domain:
ldapRealm.userDnTemplate = {0}Consider use of uppercase/lowercase spelling for domain and account
Add the ldapRealm and iniRealm like this:
securityManager.realms = $ldapRealm, $iniRealm
Add domain\account to the [users] section. Assign roles but omit passwords for LDAP authenticated users like this:
COMPANY\account = ,role [,role]
Example LDAP Configuration with several LDAP Servers
LDAP configuration with several LDAP servers is achieved by defining more than one LDAP realm as shown in the next code block.
Define two realms and assign them like this:
securityManager.realms = $ldapRealm1, $ldapRealm2
A full shiro.ini example with Group Search
A full shiro.ini example with Group Search where the member attribute does not contain the account name but the common name
A full shiro.ini example with memberOf in the account record
A public LDAP Server for testing the connection
An online public LDAP server which can be accessed using a relatively simple configuration is available from Forum Systems. This server can be used to set up a test environment with LDAP authentication. In this article we will refer to the authentication of two user accounts on this server - gauss and newton - that are each members of a different LDAP group as shown in the following table:
| Account Name | Password | LDAP Group | Shiro Role |
|---|---|---|---|
| gauss | password | mathematicians | all |
| newton | password | scientists | it_operator |
To implement the authentication configuration - or realm - for accessing this public LDAP server, add the following lines to the [main] section of the shiro.ini file:
publicLdapRealm = com.sos.auth.shiro.SOSLdapAuthorizingRealm
publicLdapRealm.userDnTemplate = uid={0},dc=example,dc=com
publicLdapRealm.searchBase = dc=example,dc=com
publicLdapRealm.contextFactory.url = ldap://ldap.forumsys.com:389
publicLdapRealm.groupNameAttribute = ou
publicLdapRealm.userNameAttribute = uid
publicLdapRealm.rolePermissionResolver = $rolePermissionResolver
publicLdapRealm.userSearchFilter = (uniqueMember=uid=%s,dc=example,dc=com)
publicLdapRealm.groupRolesMap = \
scientists : it_operator, \
mathematicians: all
rolePermissionResolver = com.sos.auth.shiro.SOSPermissionResolverAdapter
rolePermissionResolver.ini = $iniRealm
securityManager.realms = $publicLdapRealm, $iniRealm
cacheManager = org.apache.shiro.cache.MemoryConstrainedCacheManager
securityManager.cacheManager = $cacheManager
Save the modified shiro.ini file. (It is not required to restart the Jetty web server.)
You will now be able to use JOC Cockpit to authenticate the two User Account name:password combinations listed in the table above with the LDAP server.
The Shiro authentication (using, for example, the default root:root User Account) will still be active alongside the LDAP accounts listed above.
The LDAP group memberships will be mapped to the default Roles configured in the shiro.ini [roles] section as can be seen in lines 15-17 of the code listing above. This can be checked in the JOC Cockpit by looking at the Permissions section of the relevant User Profiles - the User Account gauss, for example, will have all permissions.
Logging
References
Use Cases
For debugging of LDAP Server connections











