Introduction
The JS7 - LDAP Identity Service offers authentication from an LDAP Directory Service and is available from JS7 - REST Web Service API.
- Early JS7 releases make use of the JS7 - Shiro Identity Service, for migration see JS7 - Shiro Identity Service Migration.
- The connection to an LDAP Server can be secured, see JS7 - LDAP over TLS (STARTTLS) and LDAP over SSL (LDAPS).
This article explains the steps for configuration of an LDAP Directory Service:
- Step 1: Basic LDAP Configuration
- Step 2: Authentication
- Step 3: Authorization
- Define roles
- Define groupRolesMapping
- Define the LDAP attributes to search for groups
Relevant Tools
- LDAP Browser:
- The screenshots used in this article were made with the Softerra LDAP Browser that was configured to use the relevant LDAP Directory Service.
- Command Line Client:
- The examples used in this article are executed with ldapSearch.
Preceding
The following diagram provides an overview of the steps to set up LDAP connections:
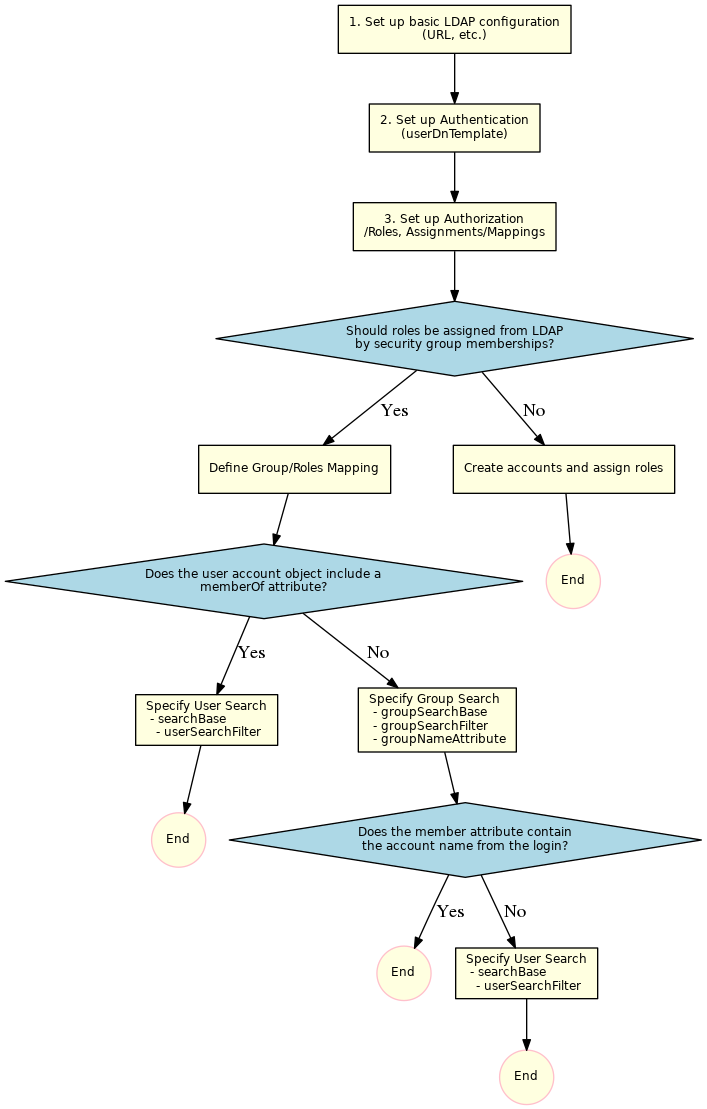
Step 1: Basic LDAP Configuration
The LDAP configuration can be managed from the Administration->Manage Identity Services view like this:
Add Identity Service
In a first step click the Add Identity Service button that brings up the following popup window.
- A Name has to be specified that identifies the LDAP Identity Service.
- The Identity Service Type gives a choice
LDAP: to map user/role assignments from security group membership in the LDAP Server,LDAP-JOC: to manage user/role assignments for the Identity Service with JOC Cockpit.
- Do not make the Identify Service Required before you are certain that the service configuration works fine.
- Select the
single-factorAuthentication Scheme.
Manage Identity Service Settings
In a next step set up the configuration of the service:
- Select the Manage Settings action menu item like this:
This brings forward a popup window with the following tabs:
- Simple Mode: The most frequently used settings are available.
- Expert Mode:: The full set of settings is available.
Specify General Settings
Find detailed explanations about general settings from JS7 - LDAP Identity Service, chapter: Identity Service Settings.
The following table lists the general items used to configure an LDAP connection.
| Name | Value | Description |
|---|---|---|
LDAP Server URL |
| The host and the port of the LDAP Server. |
LDAP Start TLS | true|false | To enable Starttls set the value to See JS7 - LDAP over TLS (STARTTLS) and LDAP over SSL (LDAPS) |
Host Name Verification | true|false | Enables host name verification for the server certificate. The default value is off. |
LDAP Truststore Path | Should the LDAP Server be configured for TLS/SSL protocols then the indicated truststore has to include an X.509 certificate specified for the Extended Key Usage of Server Authentication. | |
LDAP Truststore Password | If an LDAP truststore is used and the LDAP truststore is protected by a password, then the password has to be specified. | |
LDAP Truststore Type | If an LDAP truststore is used then the type of the indicated truststore has to be specified being either |
Step 2: LDAP Authentication
Specify Authentication Settings
The following table lists possible values for authentication with an LDAP Server:
The value {0} will be substituted with the account name.
| Name | Value | Description |
|---|---|---|
LDAP User DN Template |
| Should work from scratch for Microsoft Active Directory®. For login use |
uid={0},ou=People,dc=sos | Use with Microsoft Active Directory® and other LDAP Servers. Look up the For login use | |
cn={0},ou=Users,dc=sos,dc=berlin,dc=com | Use with Microsoft Active Directory® and other LDAP Servers. The Common Name For login use | |
uid={0},dc=example,dc=com | Use with Public LDAP Server. For login use |
Verify Authentication Settings
Step 3: Authorization
Authorization includes the assignment of roles to user accounts. Roles, in turn, hold permissions. For details see JS7 - Manage Roles and Permissions.
There are two options for assignment of roles to user accounts depending on the Identity Service Type:
LDAP: add a Group/Roles mapping. Membership of a user account in security groups of the LDAP Server is mapped to roles in the Identity Service.LDAP-JOC: add a user account and assign roles. Accounts are managed with the Identity Service in parallel to the LDAP Server. No user passwords are managed with JOC Cockpit as authentication is performed with the LDAP Directory Service.
Assign Roles with Identity Service
For details see JS7 - Manage Roles and Permissions.
Map Roles from LDAP Security Groups
If roles are assigned with JOC Cockpit by use of the Identity Service Type LDAP-JOC then you can skip this chapter.
The group/roles mapping defines a search for groups and a maps resulting groups to roles.
The search for groups can be executed with one of the following options:
- The LDAP Server makes use a memberOf attribute. In this case users can retrieve the list of groups with the User Search and should proceed with chapter Using memberOf with User Search.
- The LDAP Server does not make use of a memberOf attribute. In this case the group contains the Accounts that are members of the group. Users should proceed with chapter Using Group Search.
Substitution of the account value
In both searches with groupSearchFilter and with userSearchFilter users can specify placeholders:
- In the
groupSearchFilterand in theuserSearchFilterusers can specify the placeholder%s, for example:(uid=%s)- The placeholder
%swill be substituted with the account from the login. Users can login withdomain\accountoraccount@domain.
- The placeholder
- Users can specify the placeholder
^s, for example:(uid=^s)- The placeholder
^swill be substituted with the original value from the login, for example:account@domain.
- The placeholder
Approach 1: Using User Search to look up the memberOf Attribute
This approach looks up the account entry and reads the memberOf attribute. This attribute frequently is available from Microsoft Active Directory® LDAP Servers.
Define a userSearchFilter and a searchBase to look up the account.
Microsoft Active Directory® supporting the memberOf attribute
| Name | Value | Description |
|---|---|---|
LDAP Search Base |
| The search base for the LDAP search |
| LDAP User Search Filter | Default: (sAMAccountName=%s) |
General
| Name | Value | Description |
|---|---|---|
LDAP Search Base |
| The search base for the LDAP search |
| LDAP User Search Filter | Example: (uid=%s) |
An LDAP Browser can be used to identify the suitable values for the searchBase and the userSearchFilter. Users can perform a directory search with the value and should find a single resulting entry.
The searchBase is the value of the base DN (or ParentDN in the screenshot above).
Hint:
- If the attribute name in a user's environment does not match the default name memberOf then users can specify the name of the attribute with the
groupNameAttributeas explained below.
Approach 2: Using Group Search to look up groups that an account is a member of
If the LDAP Server makes use of the memberOf attribute then users can skip this section and proceed with chapter Using memberOf with User Search.
To specify a group search the following settings have to be specified
- LDAP Group Search Base
- LDAP Group Search Filter
- LDAP Group Name Attribute
The groupSearchBase and groupSearchFilter for example can be configured like this:
groupSearchBase = ou=Groups,dc=sosgroupSearchFilter = (uniqueMember=uid=%s,ou=People,dc=sos)
Looking up the value for the groupSearchBase
Identify the location where groups are stored in the LDAP Server, this should identify the groupSearchBase:
Looking up the value for the groupSearchFilter
When clicking a group entry (in the screenshot, cn=apl the members included should become visible:
The groupSearchFilter is configured with attr=val where attr is the name of the attribute and val is the value. In this example, the attribute is uniqueMember and the value is valuid=%s,ou=People,dc=sos, where the userid is replaced with %s. This results in:
groupSearchFilter = (uniqueMember=uid=%s,ou=People,dc=sos)
The groupNameAttribute is the name of the attribute that holds the group name.
groupNameAttribute = cn
Hint: The value of this attribute has to be used with the groupRolesMap attribute. Typical values of the attribute could be cn=groupname,ou=Groups,dc=sos .
Substitution of the account name
If roles are assigned by JOC Cockpit using the Identity Service Type LDAP-JOC you can skip this chapter.
If the value of the member of the groups contains the Account name from the login then you can skip this chapter
Sometimes the values of the member do not contain the Account Name from the login but, for example, the cn of the Account. In this case users have to search for the account first and then to specify the name of the attribute that should be used instead of the account name from the login .
To achieve this, the searchBase, userSearchFilter and userNameAttribute attributes can be specified:
searchBase = ou=People,dc=sosuserSearchFilter = (uid=%s)
Then identify the name of the attribute that contains the value for substitution. For example:
userNameAttribute = cn
Group Roles Mapping
The mapping is configured with the "Expert Mode" of the LDAP Identity Service Settings.
Note that the value of the group depends on the result of the group search. It is the value of the attribute that has been specified with the groupNameAttribute attribute. This attribute defaults to memberOf. In case that group memberships are looked up by use of the memberOf attribute of an account then the value of the memberOf attribute has to be specified, i.e. the Distinguished Names of group hits.
Example for Group Mapping with Microsoft Active Directory® and memberOf Attribute
A typical mapping when using Microsoft Active Directory® and the memberOf attribute includes to specify each group by its Distinguished Name like this:
CN=Group1,OU=SpecialGroups,OU=Groups,OU=Company,DC=sos-berlin,DC=com ==> allCN=AnotherGroup,OU=SpecialGroups,OU=Groups,OU=CompanyDC=sos-berlin,DC=com ==> adminitratorCN=Beginners,OU=SecurityGroups,OU=Groups,OU=Company,DC=sos-berlin,DC=com ==> business_user
Example for Group Mapping with cn Attribute
A mapping that is based on Group Search would apply resulting groups from the value of their Common Name like this:
sos ==> it_operatorapl ==> administrator,application_manage
The configuration will look like this:
Examples and special configurations
| userDnTemplate | groupSearchBase | groupNameAttribute | groupSearchFilter | searchBase | userNameAttribute | userSearchFilter | |
|---|---|---|---|---|---|---|---|
Group Search | uid={0},ou=People,dc=sos | ou=Groups,dc=sos | cn | (uniqueMember=uid=%s,ou=People,dc=sos) | |||
Group Search where the member attribute does not contain the account name but the common name | uid={0},ou=People,dc=sos | ou=Groups,dc=sos | cn | (uniqueMember=uid=%s,ou=People,dc=sos) | ou=People,dc=sos | cn | (uniqueMember=uid=%s,dc=example,dc=com) |
memberOf in the account record | uid={0},ou=People,dc=sos | ou=People,dc=sos | (uid=%s) | ||||
public LDAP Server | uid={0},dc=example,dc=com | ou | dc=example,dc=com | uid | (uniqueMember=uid=%s,dc=example,dc=com) |
A public LDAP Server for testing the connection
An online public LDAP server which can be accessed using a relatively simple configuration is available from Forum Systems. This server can be used to set up a test environment with LDAP authentication. In this article we will refer to the authentication of two user accounts on this server - gauss and newton - that are each members of a different LDAP group as shown in the following table:
| Account Name | Password | LDAP Group | Role |
|---|---|---|---|
| gauss | password | mathematicians | all |
| newton | password | scientists | it_operator |
Logging
References
Use Cases
For debugging of LDAP Server connections











