Introduction
Users find sensitive data such as passwords in a number of places:
- Jobs that require passwords for individual access to resources such as databases, mail servers etc.
- Credentials for JS7 - Database connections
- Credentials for JS7 - File Transfer
Generally the best way how to securely handle passwords is not to use them. However, there can be scenarios when passwords cannot be avoided. In this situation users can encrypt and decrypt sensitive data such as passwords by use of asymmetric keys.
Asymmetric Keys
Encryption and decryption make use of asymmetric X.509 Private Keys and Certificates. This includes the following roles:
- Sender: has access to the receiver's Certificate or Public Key and encrypts a secret based on the receivers's Public Key that is directly available or that can be calculated from a Certificate.
- Receiver: has access to the Private Key that allows decryption of the encrypted secret.
For creation of Encryption Keys see JS7 - How to create X.509 Encryption Keys.
Encryption
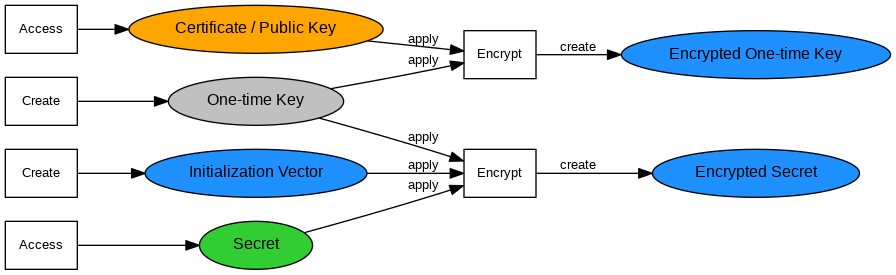
- A secret is encrypted using the Certificate or Public Key of the receiver that should decrypt the secret.
- The encryption process takes the following steps:
- Create a symmetric one-time key.
- Encrypt the one-time key with the receiver's Public Key. If a Certificate is used then the Public Key is calculated from the Certificate.
- Create an initialization vector that includes changing values for a "salt" to protect encrypted secrets from attacks using rainbow tables. The "salt" is no sensitive information, its knowledge will not allow more efficient attacks.
- Encrypt the secret with the one-time key and initialization vector.
- Drop the one-time key, only the receiver will be able to decrypt the encrypted one-time key later on.
- The outcome of encryption that is forwarded to a receiver includes the following items:
- encrypted one-time key,
- initialization vector which includes the "salt",
- encrypted secret.
Decryption
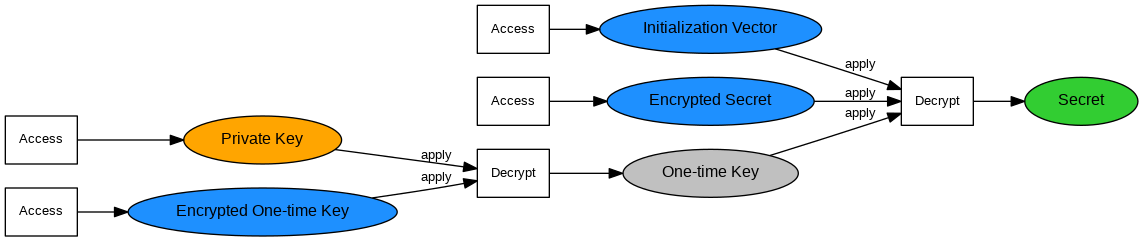
- The receiver is the sole owner of the Private Key, which guarantees that no one else can decrypt the secret.
- The decryption process takes the following steps:
- Decrypt the encrypted one-time key using the Private Key.
- Use the decrypted one-time key and initialization vector to decrypt the encrypted secret.
- Drop the one-time key.
Integration Scenarios
JS7 encryption/decryption can be integrated in a number of ways. Frequently used scenarios include:
- JS7 - Encryption - Integration with Shell CLI
- JS7 - Encryption - Integration with Secret Manager Products
Download
The JS7 encryption libraries ship with JS7 Agents that can use encyption/decryption from shell jobs. In addition, the libraries are provided for download to perform encryption and decryption outside of JS7 products.
- Download: JS7 - Download (Section: Utilities, Files:
js7.encryption.tar.gz,js7.encryption.zip) - The JS7 encryption libraries can be used from the below interfaces
- a command line interface (CLI) is available for Linux, MacOS®, AIX® using bash, zsh, dash shell, see JS7 - How to encrypt and decrypt using Unix Shell
- a CLI is available for Windows® Shell, see JS7 - How to encrypt and decrypt using Windows Shell.
- PowerShell cmdlets can be used with Linux, MacOS® and Windows®, see JS7 - How to encrypt and decrypt using PowerShell
- Encryption and decryption with PowerShell cmdlets and with the CLI for Unix Shell and Windows Shell can be used interchangeably across platforms.
The archive files of the JS7 encryption libraries (Unix: .tar.gz; Windows: .zip) hold the following files and folders:
Unix
js7.encryptionexample-*.sh: examples for creating keys and for calling encryption/decryption scriptsbinjs7_encrypt.sh: see JS7 - How to encrypt and decrypt using Unix Shelljs7_decrypt.sh: see JS7 - How to encrypt and decrypt using Unix Shelljs7_set_job_resource.sh: see JS7 - How to update a Job Resource using Unix Shell
lib3rd-party: libraries provided by 3rd-party projectssos: libraries provided by SOS
Windows
js7.encryptionexample-*.cmd: sample files for creating keys and for calling encryption/decryption scriptsbinjs7_encrypt.cmd: see JS7 - How to encrypt and decrypt using Windows Shelljs7_decrypt.cmd: see JS7 - How to encrypt and decrypt using Windows Shell
lib3rd-party: libraries provided by 3rd-party projectssos: libraries provided by SOS
Further Resources
- JS7 - How to encrypt and decrypt
- JS7 - How to update a Job Resource using Unix Shell
- JS7 - How to update a Job Resource using PowerShell
- JS7 - How to encrypt and decrypt Database Credentials
- Users who wish to check the implementation of classes for encryption/decryption find related source code from the following links: